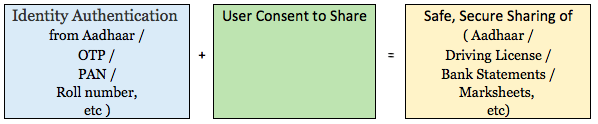
An inspiring effort in response to COVID-19
Last Tuesday, for the first time in recorded history, India pulled the emergency brakes on all of the complex interactions that make up the economy and society of 1.3 Billion Indians.
We’re going to see a lot more cascading effects of bringing almost all economic activity to a sudden and near-complete stop. Some of those effects are already visible and others will reveal themselves over time. One thing that’s easy to predict is that this disaster, like most others, will affect Bharat more than it does India.
However, at iSPIRT, we remain impatient optimists for Bharat. It does not suffice for our volunteers to simply predict the future; we want to help create it. When the lockdown hit, we could immediately see that the country’s messy supply chains would be hard-pressed to disentangle essential services from non-essential ones. On the very first day of the lockdown itself, you may have seen videos or news about the police using their lathis on innocent essential service providers like doctors.
This is undeniably tragic, but at its heart is an information and social trust issue inherent in India. When you distil the problem, it comes down to how does the administration identify those travelling for essential-services vs those who are not. Consider this, Swiggy and Zomato alone – who only work on the last mile of one category of food – claim to have a fleet of close to 500,000. For the entire supply chain, even restricted to essential items only, will require authorisations for millions of people and another few million vehicles.
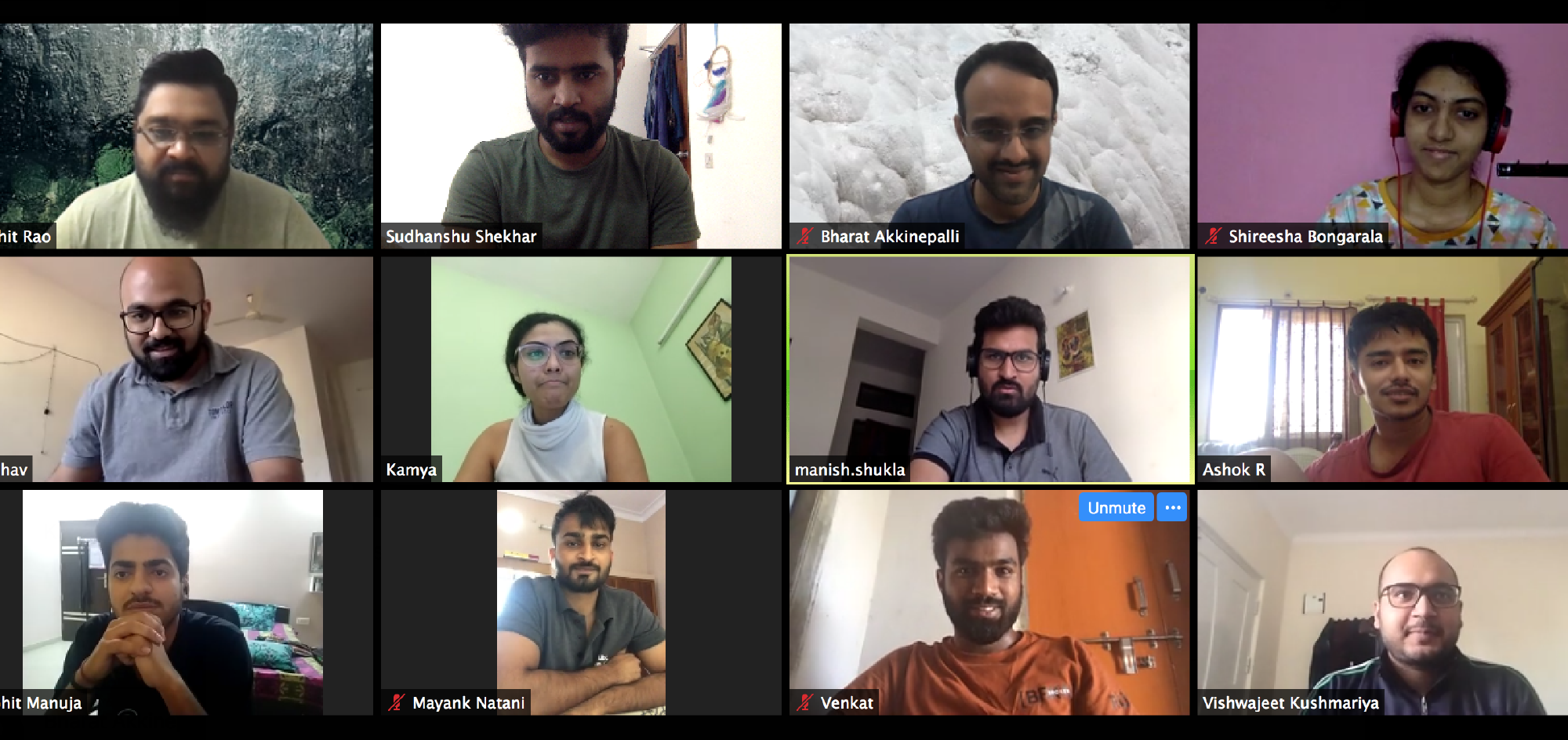
So today, we’re announcing the release of an open-source tool called, ePass. ePass is a tool to help the administration issue digital lockdown passes. These e-Passes are secure and can be verified when needed. iSPIRT got this solution going from zero to launch in less than 4 days. In the following interview, Tanuj Bhojwani speaks with Sudhanshu Shekhar, who led the effort to build the tool and Kamya Chandra, who helped liaison with the Karnataka administration.
Tanuj Bhojwani: Hey Sudhanshu, let’s start with what e-Pass is?
Sudhanshu Shekar: Sure, so the objective is to make sure that those who are on the road providing essential services or regular citizens seeking them can face minimal friction from the authorities.
We imagine a simple 4-step flow
- Individuals, such as you or me, or businesses providing essential services, can apply for a pass.
- The administration sees these requests digitally, and can authorise them from the backend, either manually or via automated rules.
- People can download their digitally signed passes on their devices
- The on-ground personnel, such as the police, can verify the curfew pass is valid by scanning it.
We’ve built tools for each part of that flow.
When we started working with the administration, they gave another great suggestion. If the beat officers could provide pre-authenticated “tokens” – like a gift-code, we could make this process even more convenient for some essential service providers. For example, they could distribute tokens to all the informal businesses in a mandi in one go, helping bring the supply-chain back online that much faster.
Tanuj Bhojwani: And you’ve made this open-source. How can a local administration use this?
Kamya Chandra: Everything is a configuration. The administration will have to decide who the approving authorities are. An admin dashboard allows bulk uploads, approvals, tracking statistics of issued passes, etc. It also allows them to configure timings, the validity of the pass, which identity fields are required, etc.
And finally, they have to instruct their beat officers to download the verification app and use it.
Tanuj Bhojwani: so the local government hosts this themselves?
Sudhanshu Shekar: Yes, the governments need to host this themselves, either directly or through a service provider. As iSPIRT, we have only provided the code and will not be providing any managed services. Even the code is open-sourced for others to use and remix as they see fit.
Tanuj Bhojwani: iSPIRT doesn’t work with the Karnataka administration normally, so how did this all happen? How did the team come together?
Sudhanshu Shekar: Sharad called me at 8 pm Tuesday or Wednesday? Maybe it was 8 in the morning. I’m no longer sure. What’s a day anyway? *laughs*
Kamya Chandra: I want to interrupt here and say I am super impressed by Sudhanshu and the rest of the team. No matter how little sleep they got, they didn’t let it affect their judgement or mood. Their decisions were always geared towards what’s the best that’s needed.
Sudhanshu Shekar: Thank you. We’re all just doing what we can.
But basically, on Monday, as Karnataka started enforcing curfew, we realised that people are going to need curfew passes. We started kicking around the idea on Monday, but there was no team. The next night the PM announced a nation-wide lockdown. We knew this was going to be a problem everywhere.
On Wednesday, the Karnataka administration also got in touch with Sharad asking for a similar solution, and they made it clear they need the solution in two days.
Sharad called and said, “I’m going to ask you about something, and you’re going to want to do it, but be really sure and think about it. This is a hard project and has very tight timelines. Everybody will understand if you say no”.
Sharad was right, I did want to do it, so I said yes and immediately got to work. I reached out to several friends and iSPIRT volunteers for help and a few – namely Mayank, Manish, Vibhav, Mohit and Ashok – agreed to help. It was easy to convince everybody, given the importance of fighting COVID. Manish has a few friends in China and was very aware about the seriousness of this situation. We quickly agreed on the basic product outline and started working. Wednesday was a flurry of activity and we got frequent reviews done with the Administration.
We realised we needed an admin console for the police to manage pass issuance. None of us was really an expert in building front-end applications and therefore, I started making calls trying to find an expert. Through referrals, I managed to reach Vishwajeet at 12 pm. I spoke to him about the project, its importance and the strict timelines. I told him we’d fail without him!
Tanuj Bhojwani: So you called a guy you’ve never met and asked him to deliver a complex task, on a ridiculous deadline for no pay nor any certificate or recognition. How did he respond?
Sudhanshu Shekar: He called his office to take a holiday. Vishwajeet sat down, worked for 15 hours straight, and delivered before time!
Kamya Chandra: *laughs* I want to add that this team, which did not know each other, did sleep shifts – including Vishwajeet, who became a volunteer that afternoon. I remember Sudhanshu taking turns with the devs to sleep at night in 2-hour batches just to keep the engine going. I’d run demos with the administration for feedback in the morning, while they all got a little shut-eye. From afternoon, they’d repeat another day and night of development.
Tanuj Bhojwani: Wow, that’s a lot of effort, and what sounds like very little sleep! What was happening on the police end, Kamya?
Kamya Chandra: Honestly, I went in with a negative impression of the police and administration – because all you see are videos of people being beaten. However, I was very impressed with the few people I was working with. They were very knowledgeable about the challenges they were going to face operationally. Also, it was obvious they were doing their best. The first call I got from them was at 11.45pm!
They made time for our demos, gave excellent, considered feedback on all of it that has definitely helped the product. For example, we added a quick and easy way to verify the ID alongside the QR, so that it can work even if the beat policeman verifying does not have a smartphone.
All of this was happening by a remote team in lockdown. I was in Delhi talking to officers in Karnataka. Other than Sudhanshu, I’ve never met any of the other volunteers! In every other organisation, this kind of a crisis response doesn’t happen as smoothly even if the team knows each other. Anywhere else, it would have been near impossible if the team didn’t know each other.
Tanuj Bhojwani: Oh! I assumed they were all from Bangalore?
Sudhanshu Shekar: No.
Mayank is in Bundi, a small town in Rajasthan. Kamya is in Delhi. I’m in Indiranagar, Bangalore. Ashok, our design guy, is in Koramangala and Mohit – I have no idea where he stays – I have never met him *everyone laughs*
Kamya Chandra: Knowing everyone’s location is harder, we still don’t know full names! One of the volunteers who helped us test the security of the product was Sasi Ganesan. I spelt his first and last name wrong in the first email I sent to him! He still helped though. On the 4th day of working together, I needed everyone’s last names, I still only knew Sudhanshu’s and Sasi’s!
Compared to the places I’ve worked before, I was surprised to see Pramod send an email with such savage truths. That’s a great example of how radical candour works, why it is in direct opposition to corporate culture.
Tanuj Bhojwani: *laughs* What were the “savage truths” in this email?
Kamya Chandra: To be fair to Pramod, it was more surprising than savage. Pramod said DO NOT GO LIVE (in bold and underline) until security and related aspects weren’t complete. The contents weren’t particularly shocking, but that he sent it to all of us – including people he barely knew. There was no secrecy or pretending to be bigger than we are. All our failures were also publicly available to a team we’ve never worked with before or met. It’s quite a unique experience.
Sudhanshu Shekar: Yeah, we were planning on going live on Friday, and we knew we needed to do security testing before we went live. Pramod’s email was a good one, and all fair asks about security, usability and data retention. He connected us to another iSPIRT volunteer, Sasi Ganesan for help. Ten hours before the scheduled launch, Sasi wrote back with a list of tasks we must do BEFORE we go live. This Thursday night email doubled our todo list. Thankfully, we were able to pull in Bharat, Sireesha and a few others from Thoughtworks to help close these tasks But at the time it felt brutal, we realised this was going to be a very hard few hours.
Kamya Chandra: Yeah, I think this is around the time Rohit started helping us enhance our UX. To me, this email was a clear indication of the high bar every iSPIRT volunteer must meet. Tight timelines or urgent needs are not enough to excuse sloppiness. I am glad we have senior volunteers such as Pramod to keep the bar high.
Tanuj Bhojwani: But I believe this story has a twist?
Kamya Chandra: Well, we did the demos in time, and everyone seemed very impressed. Unfortunately, the Karnataka administration decided to go with someone else. Their decision to go with someone else was disappointing for us.
However, they are policymakers making scale decisions. They probably had to keep many balls in the air and have redundancy. It’s good they have backup plans for backup plans.
They handled it with grace and were very kind about it. They sent a thank you and a commendation letter to each of our volunteers. One of the senior lady officers asked me – do you only take techies? I do not have a computer science degree, but I want to volunteer!
I told her I was an economist too and that she should definitely volunteer.
Sudhanshu Shekar: For me, the toughest part was when I heard the news that our work won’t be going live on Friday like I had promised all these guys. I was really sad. For about an hour, I tried to fight the decision, but then I realised that I would have to do the difficult thing and break the bad news to a bunch of volunteers who’ve slept less than 6 hours total in the last 72 hours.
What happened next is what surprised me the most about this whole thing.
All of them – every single one – took it so well! They all said something to the effect of working on a solution with other volunteers felt better than not working on one and worrying about the lockdown.
I thought this is the end of the line, but it was they who cheered me up and suggested we should open-source it. I was hoping to tell the volunteers to get some rest. Instead, these guys were so passionate that they worked for a couple more days to complete the documentation, which is why we were able to launch ePass today!
Tanuj Bhojwani: Wow. That’s quite a lot of team-spirit for a team that has never even met! So what happens now that this is open-source? How do you expect it will get traction?
Kamya Chandra: The decision to open-source paid off! Even though Karnataka didn’t take ePass, the officers messaged their batchmates and told them about what the volunteers did.
Sudhanshu Shekar: Now, we have demos scheduled with several other state governments as well as a few national ministries. We think this could be live in at least a couple of places soon.
Tanuj Bhojwani: That sounds like a fairy tale ending. Do you have any advice for anyone who is reading this and wants to volunteer?
Kamya Chandra: I used to work at the World Bank in DC, and we were trying to implement national-level digital systems in many countries. When we had technical challenges there, I was often told to get on a video call with iSPIRT volunteers for guidance and inputs. The more I interacted with them, the more I realised there is magic here to learn from. So I gave up my diplomatic passport and got on a plane to Bangalore!
So my advice is that you should try volunteering even if you’re many, many oceans away!
Sudhanshu Shekar: *laughs* I have a more straightforward test than Kamya’s for those who want to volunteer. These are also the three reasons I volunteer.
First, Societal Impact. You feel useful because you get to work on something that genuinely helps people.
Second, exposure to a wide variety of topics – such a different set of problems – you don’t exactly stick to your lane. Hence, you also meet people with very diverse backgrounds and work experiences. Because my peers are not age-bracketed with me, I feel like there are many lessons that I usually would’ve learned in ten years of my career, I’ve learned already at iSPIRT.
Third, you draw energy from others’ passion. It’s just amazing to go to work with people like this every day. I’ve realised iSPIRT is a self-selecting group – it’s only the people who seek to find it, find it. It is not easy to be a volunteer, because the environment is open and the volunteers are self-driven, people will clearly be able to see if you can walk the talk. When you have people respected in a system not for who they are, but what they do, it is magical for everyone.
Tanuj Bhojwani: That is very true. Thank you for the chat!
Like Sudhanshu says, Volunteering at iSPIRT is hard and definitely not for everyone. However, if one or more of these reasons resonate with you, you should read the volunteers handbook to learn more about balloon volunteering.