Last month, for the first time, I witnessed something really special. Even for someone like me, whose very job and calling is to evangelise this nascent software ecosystem of ours, this was something extraordinary.
I’ve been doing this a while, and what happened last month was one of the best feelings I’ve had in this journey.
This is what happened: Some of the leading B2B enterprise startups in the country, including Freshdesk, Eka Software, Capillary, Zenoti, FusionCharts, KiSSFlow, etc all got together under a single roof.
This is what they got together for: To help 52 other, smaller B2B startups in achieving scale, like they have.
It’s no exaggeration to say that the founders of these companies are some of the most important product leaders we have.
In the first session itself, Shekar Kirani pointed out that a platform like this will not be easily available, and the assembled startups needed to leverage the best from the network and from the folks who had arrived with the the express intention of helping them. And the product leaders who also made an important point – that they did not want the new age startups to go through the same grind, or make the same mistakes they had made in their years of scaling.
I was amazed. It is almost never that you see such accomplished professionals come together towards helping and nurturing young startups from their own learnings.
And what was this? What was happening?
This was the 2nd edition of #PNgrowth.
The first one had been in Jan 2016 at the Infosys Campus in Mysore where we had assembled around 186 founders to help companies think about Category Leadership. It went really, really well, but the feedback was that that perhaps keeping it focussed for fewer founders would help the cause better.
Many heated discussions were conducted over breakfast, lunch, dinner, and beer (especially beer) on the program for the 2nd edition and on how we can add value to the content.
These conversations were typically 4-6 hours long, which meant that the entire program/content took us over 200 hours with 12 founders brainstorming for the past 3-4 months.
It really did take us that long.
And those deep discussions based on the 1st edition’s feedback was what the program for November was based on.
And now that #PNgrowth 2016 is over, I decided to take a look back and share some of the learnings in organising this, and on how we pulled this together.
This year, the program was designed to help companies chase ‘Good Scale’, that is, to achieve high growth without compromising on quality. There were 52 founders with us, from all over India, and a few from outside as well.
Before we get into the details, a larger question must be addressed again, largely because it keeps getting brought up. This time, I’m trying to use a different approach to explain this. Bear with me.
WHY IS iSPIRT DOING THIS ‘MOVIE’ CALLED PNGROWTH?
iSPIRT’s mission is to make India a ProductNation. We have many initiatives like Playbook Roundtables, PNcamp, etc which are focussed around building products and helping companies achieve good scale. Although there are many accelerators in our country, very few offer value to the founders/companies. Keeping this in mind, iSPIRT wanted to do something unique and create a platform which would help companies think about growth in an effective manner. More importantly, we want to make ongoing mentorship accessible to the founders.
 The goal was to create 8-10 companies every year which would eventually go on to become $10mn revenue companies in the next 3 years.
The goal was to create 8-10 companies every year which would eventually go on to become $10mn revenue companies in the next 3 years.
WHO ARE THE DIRECTORS OF THE MOVIE?
These are the co-chairs.
The first edition of PNgrowth had just finished and I was looking for someone to be the architect for the second edition. I met Shankar Maruwada for lunch at Muffets & Tuffets and was having a completely different conversation. But, as we touched upon the PNgrowth topic, Shankar had lots of suggestions on how we could do this better. I immediately requested him to help in designing the program and helping me organise it better.. He accepted graciously, and was keen to help.
 My next request was to get Pallav Nadhani involved again. There is a reason for this. Pallav, in many ways, was the person who forced us to think around Category Leadership. The first meeting took place at Pallav’s place which went on till 2:30 am.
My next request was to get Pallav Nadhani involved again. There is a reason for this. Pallav, in many ways, was the person who forced us to think around Category Leadership. The first meeting took place at Pallav’s place which went on till 2:30 am.
By then, I had had several interactions with Aneesh Reddy, and the early playbook roundtables on Product Management had been done by him. I reached out to him and he was very keen to be part of the program and help us.
With Shankar, Pallav and Aneesh on-board, the pillars of the event were erected.
WHERE DID I FIND THE STAR CAST FOR THE MOVIE?
These, of course, were the facilitators.
Around 4-6 months in advance, we started working on the content for the event. Various topics were discussed. One thing was clear to me: Every founder had immense passion and commitment to add value to a certain topic. The format we had in mind was to make very interactive session. All of us had had enough of the ‘sage on stage’ approach. The founders were to lead sessions and work along with the participating entrepreneurs to help them extract maximum benefit.
Many discussions later, Pallav & Shankar actually started with using the frameworks & mindflips and were later joined by Girish & Aneesh. Manav & Shekhar also used the same in their session.
 It was great to see that all the facilitators did an outstanding job of delivery of the frameworks and ensured that they shared real life stories and lots of data and numbers from their companies. What was more important was that they made sure they spent time with all the attendees and ensured they received personalised attention. They were able to build a personal connect and trust within the startup community by sharing internal information even though they didn’t have to, thereby making the discussion even more credible.
It was great to see that all the facilitators did an outstanding job of delivery of the frameworks and ensured that they shared real life stories and lots of data and numbers from their companies. What was more important was that they made sure they spent time with all the attendees and ensured they received personalised attention. They were able to build a personal connect and trust within the startup community by sharing internal information even though they didn’t have to, thereby making the discussion even more credible.
WHO CAME TO WATCH THE MOVIE?
Oh, that. We had huge demand for tickets from the audience, the founders of India’s growing startup community.
 HOW DID WE THEN SELECT WHO ACTUALLY GOT TO SEE THE MOVIE?
HOW DID WE THEN SELECT WHO ACTUALLY GOT TO SEE THE MOVIE?
This time, right from Day 1, we only wanted to get select founders to be part of PNgrowth.
To begin this selection process, we laid out which stage of startups would benefit from PNgrowth. We then went on and created a list of founders and reached out to them. Apart from this, we reached out to folks from within the eco-system and got them to recommend companies to us.
Each company was recommended by atleast 2-3 founders from the PNgrowth curation team. We did zero marketing for PNgrowth except for a video, which we used to communicate to potential participants. We received overwhelming response for the event thus putting me in a fix at several situations where I had to inform founders that they have been rejected for a program/event. It was difficult, but in the interest of the event, it had to be done.

We finally had 54 founders who confirmed their participation, out of which 52 showed up for the bootcamp. These companies were divided into groups of 6 based on the type of customer/geography they were catering to.
WHERE DID WE HIRE THE SUPPORTING ACTORS?
These were the mentors, and we were able to get around 14 founders as mentors and were simply amazed by their commitment for the two and a half days of the event. Mentors were involved in all facets of the event – from intense board room discussions to the dance floor. Let me go little more deeper on the role that they played. In every session, the founders got access to few frameworks, mindflips which they had to fill and discuss with their peers + mentors. Lot of learnings were shared by mentors and it became very valuable to the founders. Very few of them tweeted from the program as everyone was busy interacting, engaging, absorbing content, but here is one of the tweets which acknowledges the mentors.
 WHAT ABOUT THE CREW?
WHAT ABOUT THE CREW?
Getting to them, the volunteers.
In my work, I get to interact with many volunteers in many initiatives, but this time the commitment and the passion with which the volunteers worked was unimaginable. Folks would go to sleep at 5am and be ready next day at 8am. They would ensure that mentors/founders have had breakfast, etc and would go an extra mile to take care that founders are focussed on their work and don’t get distracted.
Volunteers also interacted with the founders to understand if the pace/level of the sessions suited them. Lot of planning was done in advance that each and every person who is part of PNgrowth goes back with a WOW experience. I still wonder where they get so much of inspiration from.
 I don’t know if i would ever be able to do something like that. Hats off to all the volunteers who put together an awesome experience for the PNgrowth family.
I don’t know if i would ever be able to do something like that. Hats off to all the volunteers who put together an awesome experience for the PNgrowth family.
SO, WHAT WAS THE MOVIE ALL ABOUT, THEN?
Day 1
The Founders started with a cricket match between the cohorts itself.
Sharad Sharma, our guiding light, kick started the event with his words of wisdom for all the founders.
And then it began with Pallav’s session on Who are you? As founders, entrepreneurs have to pitch or sell their ideas constantly, so as to inspire the listener to believe in their dream to either fund the idea, join the team, tie up with the startup, or write about the startup. Is there a method to this? Can this be an acquired skill?
In this session, founders learnt and practiced a simple framework that enables them to improve their ability to pitch their ideas in the shortest time, to the desired target audience – VCs, journalists, co-founders, customers, business partners, and employees.
The next session was focussed on how to maximise the value of your product. If you as a founder were to increase the perceived value of your offering (Increase average MRR by 1.5X and/or reduce churn to 0.5X),how would your economics change? How would it change your CAC, margins? What would you as a founder then do differently with your product strategy, go to market strategy (positioning, marketing, channel, pricing), team/organization structure, to increase pricing by 1.5X, in the scenarios below as relevant to you. This was followed by an interactive session with the mentors.
This was end of Day 1 and then we had networking dinner, drinks, some dance and lots of conversations led by Vinod & Ashish.
Day 2
The second day was a more power packed with two sessions. To their credit, the founders were highly engrossed in their sessions, sans their mobile phones and laptops which helped in making these sessions successful.
During the first half, Girish and Aneesh engaged in an extremely fruitful session on product-market how to scale 10X with emphasis on how to establish your sales funnel and building a repeatable sales cycle. This session covered on selling processes from SMBs (by Girish) and enterprises (by Aneesh). They also shed some light on how pricing, positioning and selling varies from one geography to another.
Apart from this, Suresh also gave his insights on selling global products out of India.
 The complete session went on till almost tea break after which the candidates came back in for the third and final session by Shekhar and Manav.
The complete session went on till almost tea break after which the candidates came back in for the third and final session by Shekhar and Manav.
This session was meant to give a befitting end to the two rigorous days of activity.
While Manav spoke about how to choose your niche category and expand to other similar industries and geographies, Shekhar’s session was centred around what a VC looks for a in a startup. In the session,
Shekhar did a Q&A round with Nags and Girish on what it takes to build a successful organisation.
He also delved a bit deeper on aspects like how to choose the right market and how to intelligently figure a way out of a market and move into one that is expanding by extracting maximum business value.
Here Raghu also added his thoughts on what it takes to raise venture capital and how one should structure an organisation for a CEO to utilise his time in the most efficient manner.
Though the mentors tried to cover as much ground as possible over the two days, they took questions from audiences on anything they still might have a doubt about.
After this was a complete group photograph since some of the mentors had to leave that night. The energy of the picture speaks for itself. Before calling it a day, the founders were given tasks/homework for them to present on the final day.
Day 3
The third day, we had some inspirational stories from Sanjay Anandaram(Seedfund), Mohit Dubey (CarWale), Phanindra Sama(RedBus), Raghunandan G(TaxiForSure), Sanjay Deshpande(FortyTwo Labs). We had actually planned for only Sanjay to talk about “entrepreneurial mindset” and then we thought about inviting all of the above folks to share their energy.
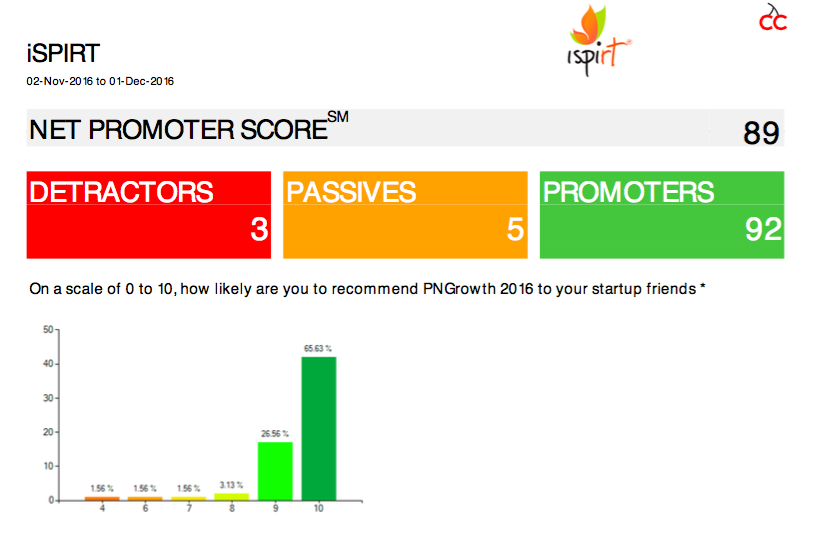
Something which we had planned for 20-30 minutes went on for around 90 mins and it was an absolute pleasure to hear some of the learnings/failures from all these founders. Below is the NPS score of 89 for PNgrowth 🙂
 After this, all founders were made to do this exercise on “Getting to 3X Growth in 12 Months”. All mentors with their cohorts spent time with the founders and helped them on what they should be thinking about this. Six Founders got an opportunity to share with the whole group.
After this, all founders were made to do this exercise on “Getting to 3X Growth in 12 Months”. All mentors with their cohorts spent time with the founders and helped them on what they should be thinking about this. Six Founders got an opportunity to share with the whole group.
Finally Shankar invited all volunteers to share few words on why they volunteered for PNgrowth. With it, a spectacular three days came to end, with some photographs and a lot of hugs, cheers, and greetings.
For me, it was a great feeling to see all of this happen, and at this scale. This probably capped off the year of 2016 for me and iSPIRT as a year in which we were actually able to make the ecosystem function as a cohesive, united entity. Lots of work is ahead of us, but as I write this, I acknowledge a task well begun.

Many thanks to Sairam for editing & Shruti for filling the blanks.